Tailored Corporate Security Solutions for Your Unique Business Needs
In today's significantly complex organization landscape, ensuring the safety and security of your organization is of extremely important significance., we acknowledge that every company has its very own distinct collection of safety and security needs. That is why we supply tailored company security solutions developed to resolve the particular obstacles and susceptabilities of your organization.
Evaluating Your Details Safety Needs
To successfully address your organization's safety issues, it is crucial to conduct a thorough evaluation of your specific safety requirements. Comprehending the distinct risks and vulnerabilities that your business faces is essential for creating an effective safety approach. Without a proper analysis, you might assign sources inefficiently or forget vital locations of vulnerability.
The very first action in assessing your particular protection needs is to carry out a thorough assessment of your physical properties, consisting of buildings, vehicle parking locations, and access factors. In addition, it is essential to assess your organization's electronic safety by assessing your network framework, data storage, and encryption procedures.
Another critical facet of examining your safety requires is recognizing your organization's special functional demands and conformity responsibilities. This includes taking into consideration elements such as the nature of your market, the worth of your possessions, and any type of lawful or regulative requirements that might apply. By recognizing these specific factors, you can customize your safety gauges to fulfill the particular demands of your business.
Tailoring Security Solutions for Optimum Defense
Personalize your security systems to provide ideal security for your organization. When it pertains to securing your company and its assets, a one-size-fits-all method just won't be sufficient. Every business has its own one-of-a-kind security demands, and tailoring your monitoring systems is crucial to making certain that you have the most effective protection in area.
Primarily, it is very important to perform a comprehensive analysis of your properties to determine at risk areas and potential safety and security risks. This will certainly help determine the type and number of electronic cameras needed, as well as their calculated positioning. Risky locations such as entrances, parking area, and storage space facilities might call for advanced monitoring innovation, such as high-resolution electronic cameras or evening vision capabilities.

Integrating your security systems with other security measures, such as accessibility control systems or alarm system systems, can additionally boost the effectiveness of your overall safety strategy. By personalizing your surveillance systems to straighten with your specific service needs, you can have satisfaction knowing that your clients, staff members, and assets are safeguarded to the max level possible.
Executing Tailored Gain Access To Control Procedures
For optimum protection, firms need to implement tailored access control actions that straighten with their special business needs. Gain access to control actions are necessary in protecting delicate details and making sure that just licensed individuals have accessibility to specific locations or sources within a company. By tailoring gain access to control procedures, companies can develop a robust safety system that properly mitigates safeguards and threats their possessions.
Implementing tailored gain access to control procedures involves numerous vital steps. A comprehensive analysis of the company's safety and security demands and prospective susceptabilities is needed (corporate security).
Accessibility control procedures can include a combination of physical controls, such as keycards or badges, as well as technological remedies like biometric verification or multi-factor verification. These measures can be applied throughout numerous access points, such as doors, gateways, or computer systems, relying on the firm's certain requirements.
Additionally, companies should develop clear policies and treatments concerning accessibility control. This includes specifying responsibilities and roles, setting up customer access degrees, consistently reviewing access advantages, and keeping an eye on accessibility logs for any suspicious tasks. Regular training and awareness programs should additionally be performed to make sure employees are aware of the relevance of gain access to control and adhere to established methods.
Enhancing Cybersecurity to Secure Sensitive Data
Implementing durable cybersecurity procedures is important to efficiently guard delicate data within a firm. In today's electronic landscape, where cyber dangers are becoming increasingly sophisticated, businesses have to focus on the security of their valuable information. Cybersecurity encompasses a range of strategies and innovations that aim to stop unauthorized access, information breaches, and other malicious tasks.
To enhance cybersecurity and safeguard delicate data, firms must implement a multi-layered strategy. Additionally, applying solid access controls, such as multi-factor authentication, can help prevent unapproved accessibility to delicate systems and information.

Moreover, companies ought to have an event response plan in position to successfully reply to and reduce any cybersecurity occurrences. This strategy ought to detail the steps to be taken in the occasion of an information violation or cyber strike, consisting of communication methods, containment steps, and recovery strategies.
Recurring Assistance and Maintenance for Your Unique Demands
To make sure the ongoing effectiveness of cybersecurity measures, continuous assistance and This Site upkeep are important for dealing with the progressing hazards faced by organizations in guarding their delicate data. In today's rapidly altering electronic landscape, cybercriminals are frequently finding brand-new means to make use of susceptabilities and violation safety systems. For that reason, it is vital for organizations to have a durable directory support and upkeep system in position to remain in advance of these risks and secure their useful details - corporate security.
Recurring assistance and maintenance involve frequently covering and updating protection software application, keeping track of network tasks, and performing vulnerability assessments to recognize any weaknesses in the system. It also consists of giving timely support and advice to workers in carrying out safety and security finest techniques and reacting to potential safety events.
By purchasing continuous assistance and maintenance solutions, organizations can gain from aggressive monitoring and discovery of possible hazards, in addition to prompt reaction and removal in the event of a protection breach. This not only aids in minimizing the influence of an assault but additionally makes certain that the organization's security posture continues to be strong and adaptable to the evolving danger landscape.
Final Thought
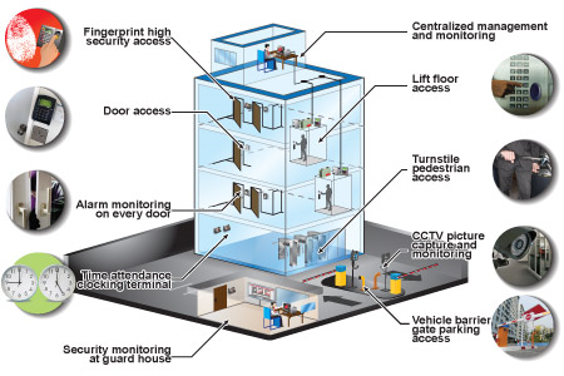
To efficiently address your company's safety and security problems, it is vital to carry out a detailed evaluation of your particular security demands. Every organization has its own distinct protection requirements, and customizing your surveillance systems is vital to guaranteeing that you have the most efficient security in area.
For ideal protection, business need to execute customized accessibility control steps that align with their special organization requirements.In verdict, tailored corporate security remedies are crucial for companies to resolve their unique security requirements. By examining details safety and security needs, customizing security systems, executing tailored gain access to control procedures, and improving cybersecurity, businesses can safeguard sensitive data and shield versus potential risks.